What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-04-03 18:09:04 | APT10 - Operation Cloud Hopper (lien direct) | Written by Adrian Nish and Tom RowlesBACKGROUNDFor many businesses the network now extends to suppliers who provide management of applications, cloud storage, helpdesk, and other functions. With the right integration and service levels Managed Service Providers (MSPs) can become a key enabler for businesses by allowing them to focus on their core mission while suppliers take care of background tasks. However, the network connectivity which exists between MSPs and their customers also provides a vector for attackers to jump through. Successful global MSPs are even more attractive as they become a hub from which an intruder may access multiple end-victim networks.Since late 2016 we have been investigating a campaign of intrusions against several major MSPs. These attacks can be attributed to the actor known as APT10 (a.k.a. CVNX, Stone Panda, MenuPass, and POTASSIUM). Their activity seems to have increased in mid-2016, and has focused on compromise of MSPs as a stepping stone into victim organisations.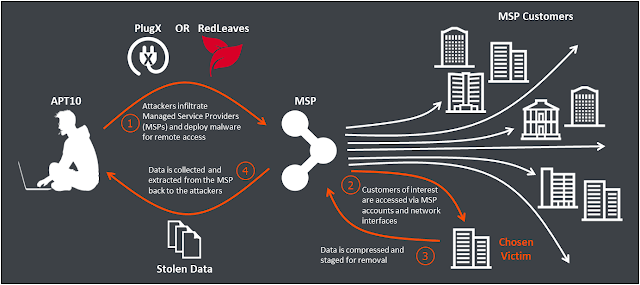 Figure 1 – Attack stages for APT10 in targeting MSP end-customersWe have joined forces with PwC to release our findings from investigations into these on-going attacks and raise awareness. This joint analysis report can be found on PwC's blog at:https://www.pwc.co.uk/issues/cyber-security-data-privacy/insights/operation-cloud-hopper.htmlOVERVIEWThe current campaign linked to APT10 can be split into two sets of activity:1. Attacks targeting MSPs, engineering and other sectors with common as well as custom malware;2. Attacks targeting Japanese organisations with the 'ChChes' malware;The latter campaign has been well covered in the public domain, however the MSP targeting is the focus of our joint analysis report with PwC.The group use a custom dropper for their various implants. This dropper makes use of DLL side-loading to execute the main payload.In our analysis the attackers have used several payloads including:1. PlugX – a well-known espionage tool in use by several threat actors2. RedLeaves – a newly developed, fully-featured backdoor, first used by APT10 in recent monthsINFRASTRUCTUREThe C&C domains chosen by the APT10 actors for their MSP-related campaign are predominantly dynamic-DNS domains.The various domains are highly-interconnected through shared IP address hosting, even linking back historically to the group's much older operations. The graph below depicts infrastructure used by the attackers in late 2016. Figure 1 – Attack stages for APT10 in targeting MSP end-customersWe have joined forces with PwC to release our findings from investigations into these on-going attacks and raise awareness. This joint analysis report can be found on PwC's blog at:https://www.pwc.co.uk/issues/cyber-security-data-privacy/insights/operation-cloud-hopper.htmlOVERVIEWThe current campaign linked to APT10 can be split into two sets of activity:1. Attacks targeting MSPs, engineering and other sectors with common as well as custom malware;2. Attacks targeting Japanese organisations with the 'ChChes' malware;The latter campaign has been well covered in the public domain, however the MSP targeting is the focus of our joint analysis report with PwC.The group use a custom dropper for their various implants. This dropper makes use of DLL side-loading to execute the main payload.In our analysis the attackers have used several payloads including:1. PlugX – a well-known espionage tool in use by several threat actors2. RedLeaves – a newly developed, fully-featured backdoor, first used by APT10 in recent monthsINFRASTRUCTUREThe C&C domains chosen by the APT10 actors for their MSP-related campaign are predominantly dynamic-DNS domains.The various domains are highly-interconnected through shared IP address hosting, even linking back historically to the group's much older operations. The graph below depicts infrastructure used by the attackers in late 2016. Figure 2 – Infrastructure view from late 2016In recent months the infrastructure has expanded significantly. The nodes number into the thousands and cannot be easily visualised.The below graph represents a linkage between one of the PlugX C&Cs used in the group's newer ope Figure 2 – Infrastructure view from late 2016In recent months the infrastructure has expanded significantly. The nodes number into the thousands and cannot be easily visualised.The below graph represents a linkage between one of the PlugX C&Cs used in the group's newer ope |
APT 10 APT 1 |
1
We have: 1 articles.
We have: 1 articles.
To see everything:
Our RSS (filtrered)
